Abstract
Digital image processing, a subset of digital signal processing, has widespread adoption across various fields due to its versatility and benefits. Leveraging computer science, programming, and artificial intelligence, enables the manipulation and analysis of digital images to extract valuable information. This paper explores the extensive applications of digital image processing techniques, encompassing areas such as image sharpening and restoration, medical imaging, remote sensing, robotics, color processing, pattern recognition, and more. With its extreme flexibility, digital image processing facilitates linear and nonlinear processes, catering to diverse needs across disciplines. Moreover, the advancements in image processing systems contribute to improving pictorial information for human interpretation and enable autonomous machine perception through enhanced image data storage, transmission, and representation. This paper aims to define the scope of digital image processing, elucidate its methodologies, and showcase its pivotal role in advancing research across frontier areas.
Keywords
Image Classification System, Digital image processing
Introduction
In today’s technologically advanced landscape, computers have become indispensable tools for facilitating control over engineering systems, data collection, analysis, processing, and decision-making processes across various industries. Digital image processing, a fundamental branch of computer science, is dedicated to manipulating digital signals representing images captured by digital cameras or scanners. Formerly known as image processing, its integration with computer technology underscores its pivotal role in intelligent systems where critical decisions are made.Digital image processing encompasses numerous applications across technical, industrial, urban, medical, and scientific domains. Its primary branches focus on image enhancement and machine vision. These techniques aim to improve visual quality, ensure accurate display environments, and interpret image content for purposes such as robotics and image analysis. In essence, digital image processing processes two-dimensional signals to extract meaningful information, serving as a cornerstone for understanding and manipulating visual data in the digital era. An image is defined by the mathematical function f(x,y)f(x, y)f(x,y), where xxx and yyy represent the two coordinates horizontally and vertically. Image processing involves operations to enhance images or extract useful information. Rapid advancements in image processing systems hold the promise of developing ultimate machines capable of performing visual functions akin to those of living beings.
Some major fields in which digital image processing is widely used are mentioned below.
Security purposes:
Image sharpening and restoration for the Medical field, Remote sensing Transmission and encoding Machine, Robot vision Color processing, Pattern recognition Video processing Microscopic Imaging.
LITREATURE SURVEY
Digital image processing involves various stages designed to manipulate images for a range of purposes, which can be broadly categorized into two areas: methods that provide image inputs and outputs, and those that extract attributes from images. The process begins with image acquisition, often followed by preprocessing steps such as scaling. Image enhancement seeks to reveal obscured details or emphasize features of interest, though this process can be subjective. In contrast, image restoration relies on mathematical models of image degradation to achieve objective improvements. Color image processing focuses on studying color models and processing techniques in digital domains, an increasingly important area due to the growing prevalence of digital images. Wavelets play a significant role in facilitating image processing tasks.
representation and compression. Compression techniques are essential for effective storage and transmission of images, frequently utilizing established standards such as JPEG. Morphological processing plays a key role in extracting components that are vital for shape representation. Segmentation is an important yet challenging task that involves partitioning images, laying the groundwork for subsequent processing stages. Following segmentation, representation and description transform raw image data into forms that are more suitable for computer analysis. Recognition then assigns labels to identified objects based on their descriptors, which is fundamental for effective object identification. Additionally, geometric adjustments and various processing techniques, including security measures, contribute to enhancing both the quality and security of images.
Image processing can be categorized into three general levels:
1. Low-level processing: This category involves basic tasks such as noise cancellation, image filtering, and contrast adjustments.
2. Intermediate-level processing: In this phase, the input is typically an image, while the output consists of attributes related to image objects, such as edges, contours, and object recognition.
3. High-level processing: This advanced stage entails understanding the relationships between detected objects, interpreting scenes, and performing analyses akin to those carried out by the human visual system.
The field of image processing encompasses a variety of techniques aimed at manipulating images for diverse applications, including picture processing, pattern recognition, and image interpretation. Picture processing focuses on improving image quality by addressing issues like overexposure, underexposure, and blurriness, often using techniques such as contrast enhancement. Pattern recognition involves generating descriptions or classifying images into specific categories, exemplified in applications like automatic mail sorting. Given the rise of digital information, it is critical to view image processing within the broader context of information processing, where images play a pivotal role.
Enhancement and restoration techniques further contribute to image quality improvement. Enhancement methods like contrast modification, blurring correction, and noise removal aim to refine image clarity, while restoration techniques are dedicated to correcting specific forms of degradation, often relying on formal methods like filter theory. Segmentation techniques help break images into segments to facilitate data compression and analysis, whereas feature extraction identifies specific characteristics be they natural or artificial within images for further processing or retrieval.
In the domain of defense surveillance, image processing is particularly valuable for monitoring land and ocean environments through aerial surveillance methods. Segmenting objects in aerial imagery allows for effective parameter extraction, assisting in the classification and localization of objects such as naval vessels. Content-based image retrieval plays a crucial role in efficiently searching and retrieving images from extensive databases based on their intrinsic content. Moreover, moving-object tracking is essential for measuring motion parameters and obtaining visual records, typically employing motion-based predictive techniques. Understanding the neural aspects of the visual sense illuminates how optic nerves convey signals and how the brain processes visual information, highlighting the significance of differentiating in contrast phenomena and the brain's integral role in perception.
Image Acquisition, Preprocessing, and Feature Extraction
Creating a facial recognition system to identify familiar soldiers and mark unknown individuals as potential threats demands careful execution at every stage. Below is a detailed overview of the processes involved:
Image Acquisition
This initial phase involves capturing raw image data from various input sources.
Challenges and Considerations:
Cameras: High-resolution CCTV or specialized security cameras.
Infrared or Thermal Cameras: Beneficial for low-light or nighttime situations.
Video Streams: Ongoing footage needed for frame-by-frame analysis.
Lighting Variations: Systems should manage low light, glare, and shadowed areas.
Camera Angle and Distance: Faces need to be effectively captured from various angles and distances.
Occlusions: Manage situations where faces may be partially obstructed (e.g., by helmets, masks, or natural barriers).
High-Resolution Cameras: Ensure that the images captured have enough detail for reliable recognition.
Processing Unit: Use edge devices for preliminary processing to minimize bandwidth usage if using cloud processing.
Recommendations:
- Utilize PTZ (Pan-Tilt-Zoom) cameras for dynamic tracking of faces.
- Implement real-time video processing algorithms to identify frames containing faces.
Preprocessing
Raw images must be refined and standardized to provide consistent input for the machine learning model.
Techniques and Steps:
- Face Detection: Use algorithms like Haar cascades, HOG+SVM, or DNN-based detectors (e.g., MTCNN or RetinaFace) to find faces. Crop and align the identified faces for subsequent processing.
- Noise Reduction: Apply filters (e.g., Gaussian or median filters) to eliminate noise caused by environmental or hardware factors.
- Normalization: Adjust brightness and contrast to manage lighting variations. Convert the image to grayscale if color is unnecessary, which reduces computational demand.
- Resizing: Resize faces to a uniform input size needed by the ML model (e.g., 128x128 pixels for facial embeddings).
- Augmentation (Optional): Generate variations (rotated, scaled, mirrored) for improved robustness during training or inference.
- Landmark Alignment: Identify key landmarks (eyes, nose, mouth) to geometrically align faces for consistency.
Challenges Addressed:
This resolves inconsistencies stemming from different environments and ensures uniformity in the data, minimizing the risk of bias due to low-quality input images.
Tools/Frameworks:
- Use OpenCV for preprocessing functions.
- Employ Dlib for face alignment and landmark detection.
- Utilize Python libraries such as Pillow and scikit-image for general image processing.
Feature Extraction
This phase focuses on transforming the preprocessed image into a concise and meaningful representation for classification or recognition.
Techniques:
- Traditional Approaches:
- HOG (Histogram of Oriented Gradients): Captures the structure and orientation of facial features. It is computationally lighter but may struggle with complex variations.
- LBP (Local Binary Patterns): Gathers texture information for representing facial features.
- Deep Learning-Based Approaches:
- Use pre-trained CNN architectures (e.g., VGGFace, FaceNet, ArcFace, or DeepFace) for extracting embeddings.
- Embeddings are fixed-dimensional vectors representing facial characteristics for comparison.
- Utilize transfer learning to fine-tune models on a dataset of known soldiers to enhance accuracy.
- Extract features directly from intermediate layers of CNNs.
Key Features:
- Global Features: The overall shape and structure of the face.
- Local Features: The eyes, nose, mouth, and the distances between them.
- Temporal Features (if video): Monitor changes in expressions across frames for greater accuracy.
Image Classification
Classification in an image processing system is essential for enabling the automatic identification and categorization of objects, scenes, or patterns in images. It forms a fundamental part of various practical applications, such as medical diagnosis, facial recognition, self-driving cars, and content moderation.
Importance of Classification in Image Processing Systems
- Automating Decision-Making:
Classification empowers the system to make decisions based on data without requiring human input. For example, in medical imaging, it can categorize X-rays or MRI scans into classifications like "normal" or "abnormal."
- Enhanced Accuracy and Efficiency:
By utilizing machine learning algorithms, image classification achieves higher accuracy compared to manual methods and can process large volumes of data more quickly.
- Scalability:
Automated classification systems handle vast amounts of image data efficiently, making them suitable for content moderation on social media or satellite imagery analysis.
- Custom Applications:
Classification systems can be tailored to meet specific domain needs, such as differentiating between various animal species in ecological research or spotting defective items in manufacturing.
- Foundation for Advanced Systems:
Classification often serves as the groundwork for more sophisticated systems, such as object detection (determining object locations within an image) or segmentation (isolating objects from their background).
Steps in Developing an Image Classification System
- Problem Definition:
Clearly define the objective (e.g., identifying disease in plant leaves) and the categories (e.g., healthy, diseased).
- Data Collection:
Gather labeled image data representative of the classification task.
Tools: Digital cameras, satellite systems, or online datasets (e.g., CIFAR, ImageNet).
- Preprocessing:
Resize, normalize, and augment images (e.g., flipping, rotating) to ensure consistency and enhance the diversity of the training set.
- Feature Extraction:
Use machine learning models or techniques to extract relevant features (e.g., edges, textures, or specific patterns).
- Model Selection:
Choose a classification algorithm:
Traditional Methods: Support Vector Machines (SVMs), Random Forests.
Deep Learning Methods: Convolutional Neural Networks (CNNs), Vision Transformers (ViTs).
- Training: Train the model using labeled data, optimizing its ability to distinguish between categories.
- Validation and Testing: Evaluate the model on unseen data to ensure generalization.
- Deployment and Monitoring: Deploy the model into production and monitor its performance, periodically retraining as new data becomes available.
Different Methods of Image Recognition and Image Compression
Image processing techniques encompass a broad array of methods used for diverse applications, ranging from basic noise reduction and image filtering to more advanced tasks like object recognition and scene interpretation. These techniques are categorized into three main levels:
- Low-Level Processing:
Fundamental operations such as noise cancellation, image filtering, and contrast adjustment.
- Intermediate-Level Processing:
Extracting attributes of image objects, including edges, contours, and facilitating object recognition.
- High-Level Processing:
Understanding the relationships between detected objects, inferring scenes, and performing interpretations similar to the human visual system.
Techniques and Applications in Image Processing
- Image Zoning:
Partitioning image pixels into areas with similar brightness, texture, or color, essential for applications like image therapy, machine vision, and object science.
- Object Recognition:
Employing sophisticated algorithms and neural networks to analyze and classify images. Advanced face recognition systems using Convolutional Neural Networks (CNNs) have significantly improved detection accuracy.
- Edge Recognition:
Identifying object boundaries, which is vital for image analysis and machine vision tasks.
Image Compression
Image compression methods are critical for minimizing storage and transmission requirements. Widely used techniques like JPEG and MPEG employ tailored compression algorithms for still images and moving pictures, respectively. Image resolution encompasses pixel resolution, spatial resolution, and temporal resolution, all of which play a crucial role in determining the clarity and detail of images. Spatial resolution affects the ability to distinguish between closely spaced objects, while temporal resolution impacts the accuracy of motion representation in videos.
System Development and Validation
When creating and validating an image processing system intended to recognize known soldiers while marking unrecognized individuals as potential threats, it is crucial to focus on accuracy, fairness, and robustness. Below is a comprehensive overview of the development and validation of this system tailored to its specific application.
System Development
1. System Architecture
- Face Detection Module:
Detects faces in images or video feeds.
Example: Implement models such as MTCNN, Haar Cascades, or YOLO for face detection.
- Face Recognition Module:
Compares detected faces against a database of known soldiers.
Example: Utilize pretrained deep learning models like FaceNet, ArcFace, or Dlib’s face embeddings.
- Threat Classification Module:
Identifies unrecognized faces for additional analysis or action.
Example: A binary classifier that differentiates between "Known" and "Unknown."
2. Data Pipeline Design
- Data Sources:
- Photographic records of soldiers, including various poses, lighting conditions, and timings.
- Controlled real-world scenarios to replicate field conditions (e.g., dusty environments, changing lighting).
- Preprocessing Steps:
- Standardize image sizes.
- Address variations in lighting, expressions, and obstructions using methods like histogram equalization or GAN-based augmentation.
- Data Augmentation:
Implement augmentations such as rotation, scaling, flipping, and occlusion to enhance the model's resilience to real-world conditions.
3. Model Development
- Baseline Model:
Leverage transfer learning with pretrained face recognition models. Refine the model using a labeled dataset of soldier faces.
- Database Management:
Create an encrypted and scalable face embedding database for rapid matching.
- Confidence Thresholding:
Establish a threshold for similarity scores to assess whether a face corresponds to a known soldier.
- Scalability and Deployment:
Edge Devices: Deploy efficient models on edge devices like drones or security cameras for real-time processing.
Cloud Integration: Transfer resource-intensive tasks (e.g., training and complex validation) to the cloud.
Latency Optimization: Enhance processing times for instantaneous threat detection, taking hardware limitations into account.
System Validation
1. Model Performance Validation
- Accuracy Metrics:
Utilize Precision, Recall, and F1-Score to balance the compromise between false positives (flagging known soldiers) and false negatives (overlooking a threat). Use specific metrics for face recognition, such as True Acceptance Rate (TAR) and False Acceptance Rate (FAR).
- Generalization Testing:
Evaluate the model against unseen data with different lighting, camera angles, and occlusions to ascertain robustness.
2. Robustness Testing
- Adversarial Testing:
Conduct simulations of adversarial attacks like spoofing with photos or masks and assess the system’s defense capabilities.
- Environmental Testing:
Test the system in real-world situations (e.g., low lighting, moving subjects).
. Ethical and Bias Validation
- Bias in Training Data:
Ensure diverse facial feature representation to prevent biases against specific ethnic groups, genders, or attributes.
- Decision Transparency:
Employ explainability tools (e.g., SHAP or LIME) to clarify reasons behind flagging certain faces.
4. Scalability and Stress Testing
- Load Testing:
Test the system under increased load (e.g., multiple cameras relaying data concurrently).
- Scaling Strategies:
Implement containerization (Docker, Kubernetes) to dynamically adjust resources during peak usage.
5. Security Validation
- Database Security:
Secure the facial embeddings database with encryption to deter unauthorized access.
- System Hardening:
Protect against cyber threats by assessing the system’s resilience to data breaches and tampering.
6. Real-World Validation
- Field Trials:
Perform tests in real operational environments like checkpoints or patrols.
- Feedback Loop:
Gather input from operators and security personnel to iteratively enhance the system.
Resources Needed
1. Data Resources
- A comprehensive, annotated dataset of soldier faces featuring various conditions.
- Additional data for augmentation to manage occlusion, lighting, and environmental differences.
2. Computational Resources
- Hardware: Optimal GPUs for training and edge devices for deployment.
- Cloud Platforms: Utilize AWS, GCP, or Azure for enhanced scalability.
- Tools and Frameworks:
Face Recognition Libraries: FaceNet, Dlib, or DeepFace.
ML Frameworks: TensorFlow, PyTorch, or OpenCV.
Monitoring Tools: Prometheus for system oversight and MLflow for model tracking.
3. People
- Domain Experts: Military personnel to affirm the system's operational significance.
- ML Engineers: To refine the face recognition model and enhance performance.
- Ethics Team: To supervise bias reduction and ensure fairness.
4. Processes
- Conduct regular audits of training data and validation procedures.
- Establish a CI/CD pipeline to facilitate swift and secure updates and corrections.
Functioning of the Model
The model employs YOLOv8, an advanced framework for real-time object detection, to identify soldiers within images. The accompanying code demonstrates a comprehensive process for performing inference on both photographs and live video feeds using a custom-trained YOLOv8 model. A custom dataset was annotated with the assistance of Roboflow to accurately label instances of soldiers. This section elaborates on the code’s operation and its significance concerning the output image, where soldiers are marked with bounding boxes.
How YOLOv8 Functions
YOLOv8 (You Only Look Once, version 8) builds on the progress of previous versions, focusing on both speed and precision. The model analyzes an image in a single pass through a deep neural network, dividing it into grid cells while predicting bounding boxes, class probabilities, and object confidence scores.
The main components of YOLOv8 are as follows:
- Image Preprocessing:
The input image is resized to a specified dimension (e.g., 640x640 pixels) to meet the model's input criteria.
Normalizing pixel values ensures uniform input scaling for consistent performance.
- Feature Extraction:
A backbone network, such as CSPDarknet, extracts features from the image.
Various layers capture distinct attributes, ranging from edges to intricate textures.
- Prediction Layers:
The model predicts bounding boxes, objectness scores, and class probabilities for every grid cell.
Post-processing methods, such as Non-Maximum Suppression (NMS), remove overlapping boxes and retain the most relevant predictions.
Output
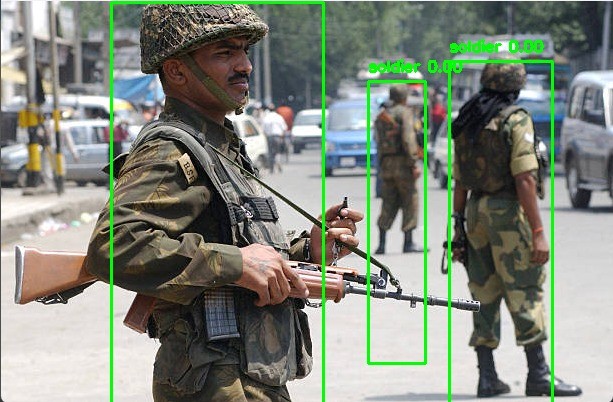
Image (a) Showing the image of multiple identified soldiers
The model generates the coordinates of bounding boxes, class IDs, and confidence scores for each detected object. In the resulting image, bounding boxes surrounding the identified soldiers are shown, with labels like "soldier 0.00" illustrating these predictions. The confidence score reflects the model’s certainty about its detection.

Image (b) Showing the image of one identified soldier among many “unknown” individuals
Here, Image(b), tells us that the trained model can respond correctly to complex situations by distinguishing perfectly, where there are unidentified individuals (labeled “unknown 0.00”) along with the identified soldiers. It signifies that the model is thoroughly trained over a large dataset of soldiers in uniform as well as the images of unidentified civilians.
The essence of the application focuses on:
- Object Detection:
A YOLOv8 model, trained on a specialized dataset, predicts bounding boxes, object categories, and confidence levels for recognized items.
- Visualization:
Predictions (bounding boxes and labels) are superimposed directly onto frames, whether images or live video.
- Graphical User Interface (GUI):
A user-friendly GUI, developed with Tkinter, enables users to engage with the program effortlessly, eliminating the need to interact with the underlying code.
Workflow
- Loading the Model:
The application begins by loading a pre-trained YOLOv8 model.
This model has been fine-tuned on a dataset specifically designed to detect Indian soldiers, providing knowledge of object categories and the ability to generalize detections to new images or video streams.
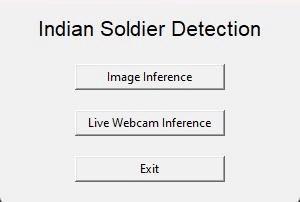
Image(c) Providing the user with 2 alternatives: (i) Image inference and (ii) Live Webcam Inference
Processing Images
(i) When a User Selects an Image:
- The image is read and submitted to the YOLOv8 model for inference.
- The model analyzes the image to predict:
- Bounding Boxes: Rectangles surrounding detected items.
- Confidence Scores: The model's assurance regarding the detection.
- Class Labels: Names for the identified objects (e.g., "soldier").
- The predictions are overlaid on the image using rectangles and labels for visualization.
- The marked image is displayed in a pop-up window for the user to view.
(ii) Processing Live Webcam Feed:
- When the live webcam mode is activated:
The program captures video frames in real time.
Each frame is analyzed by the YOLOv8 model for inference.
Predictions (bounding boxes, labels, and scores) are superimposed onto the live video feeds.
The marked frames are shown in a continuous video stream until the user exits the application.
User Interaction
The GUI provides a straightforward method to access the program's features:
Buttons enable users to select an image or initiate the webcam feed.
A separate button allows the user to terminate the application.
Key Features
-
- Custom Object Detection: The model identifies soldiers using a YOLOv8 framework fine-tuned on relevant data.
- Real-Time Inference: The application handles both static images and live video streams with real-time object detection capabilities.
- Visualization: Detected items are graphically represented with bounding boxes and labels, providing immediate feedback to the user.
- Ease of Use: The Tkinter GUI ensures accessibility, allowing users to engage without needing to interact with code or command lines.
How It Relates to the Output
- In the output, soldiers are recognized in an image, with bounding boxes drawn around them and labeled as "soldier."
- The program achieves this by:
Employing YOLOv8 to identify features in the image corresponding to soldiers.
-
- Extracting bounding box coordinates, confidencelevels, and class labels for each detection.
Rendering the predictions on the image using OpenCV.
General Workflow
- Program Start:
The model is loaded, and the GUI is set up.
- User Action:
If the user selects an image, it is processed and displayed with detections.
If the user initiates the live feed, the webcam stream is processed frame-by-frame for real-time detection.
- End of Session:
The program exits smoothly when the user selects the exit option.
Drawbacks
1. Performance Gaps
Challenge:
- Conditions like low lighting, occlusions (e.g., face coverings), and complex backgrounds can impair system accuracy.
- Variations in facial features due to expressions, aging, or injuries further complicate recognition tasks.
Impact:
- Increased false positives (mistaking known soldiers as threats).
- Missed detections (failing to identify unrecognized individuals).
Approach to Address:
- Employ robust facial recognition models, such as those based on ResNet architectures or fine-tuned Vision Transformers.
- Use data augmentation techniques (e.g., simulate low-light or occlusion scenarios during training).
- Leverage transfer learning with extensive datasets like MS-Celeb-1M or tailored military datasets.
- Utilize infrared or multi-spectral imaging to enhance low-light accuracy
2. Real-Time Challenges
Challenge: Dynamic environments, such as border patrol or battlefield operations, require real-time processing. Latency can delay threat recognition.
Impact:
Delayed recognition may provide adversaries with a strategic advantage.Real-time demands strain computational resources.
Approach to Address:
Use optimized deep learning models like MobileNetV3.
Employ hardware accelerators like NVIDIA Jetson Nano or Coral Edge TPU for edge processing.
- Apply quantization techniques (e.g., convert floating-point models to INT8) for faster inference.
- Develop efficient pre-processing pipelines to minimize delays.
3. Scalability Issues
Challenge:
- Growing soldier databases and diverse data sources (e.g., live feeds, stored images) can strain systems.
Impact:
- Reduced throughput and slower response times.
- Difficulties integrating additional modules (e.g., new camera systems).
Approach to Address:
- Adopt scalable architectures with distributed computing frameworks like Apache Spark or Kubernetes.
- Use cloud services like AWS Rekognition or Azure Face API for scalable recognition and storage.
- Develop modular pipelines for new sensor integrations.
- Implement incremental learning to adjust models without full retraining.
4. Resource Constraints
Challenge:
- Advanced models (e.g., transformers, large CNNs) are resource-intensive, making edge deployment on drones or handheld devices challenging.
Impact:
- Increased power consumption and costs.
- Limited usability in remote or resource-constrained environments.
Approach to Address:
- Use lightweight models like SqueezeNet or MobileNet.
- Apply model compression techniques (e.g., pruning, quantization, knowledge distillation).
- Enhance energy efficiency with edge AI platforms (e.g., Qualcomm Snapdragon, NVIDIA Xavier).
- Investigate federated learning to shift computations to a central server while keeping sensitive data local.
5. Integration Deficiencies
Challenge:
- Military applications often require combining data from multiple sources (e.g., cameras, LiDAR, RADAR). Integration of these data types is complex.
Impact:
- Reduced effectiveness in challenging environments (e.g., fog, heavy rain).
- Missed opportunities for improved threat detection using multi-source data.
Approach to Address:
- Develop sensor fusion algorithms to combine data from cameras, LiDAR, and RADAR.
- Use deep multimodal networks to learn features from diverse data types.
- Implement standardized APIs for hardware integration.
- Test system performance under various conditions using synthetic multimodal datasets (e.g., CARLA for autonomous systems).
FUTURE WORK
System Design and Development
Pipeline Implementation
1. Image Acquisition
- Hardware Integration: Use high-resolution cameras for real-time image capture.
- Environmental Considerations: Ensure effective image acquisition under diverse lighting and weather conditions.
- Data Flow: Securely transmit captured images to the processing unit.
2. Preprocessing
- Normalization: Standardize image size, resolution, and format.
- Noise Removal: Apply filters to reduce environmental noise.
- Face Alignment: Utilize landmark detection for consistent face alignment.
3. Feature Extraction
- Deep Features: Use pre-trained models (e.g., FaceNet, VGGFace) to obtain face embeddings.
- Custom Features: Fine-tune models with military-specific datasets for enhanced soldier recognition.
4. Object Detection
- Face Detection Algorithms: Implement models like MTCNN.
- Multi-Person Detection: Optimize models to ensure accurate recognition in crowded scenarios.
System Architecture
- Modular Design: Enable independent upgrades and integrate APIs for external communication.
Real-Time Processing Capabilities
1. High-Speed Processing
- Model Optimization: Quantize models to reduce computational load while maintaining accuracy. Remove unnecessary layers to improve inference speed.
- Hardware Acceleration: Use GPUs, TPUs, or FPGAs for deep learning tasks and leverage libraries like NVIDIA TensorRT.
2. Edge Deployment
- On-Device Processing: Deploy models on edge devices for low-latency processing.
- Network Efficiency: Use lightweight protocols to transmit essential data to central servers.
3. System Scalability
- Develop a scalable infrastructure with cloud platforms.
- Implement real-time streaming pipelines.
4. Latency Optimization
- Minimize preprocessing delays.
- Batch process images when possible to improve throughput.
Dataset Preparation and Training
1. Dataset Collection and Annotation
- Data Sources: Gather diverse images of soldiers in various conditions.
- Annotation Tools: Annotate images using tools like Labelbox or CVAT.
- Ethical Considerations: Ensure consent and privacy during data collection.
2. Data Augmentation
- Use techniques like rotation, occlusion simulation, and color adjustments.
- Employ generative models to create synthetic data for rare scenarios.
Model Training
1. Transfer Learning: Start with pre-trained models and fine-tune them for the specific task.
2. Custom Architecture: Design specialized architectures for accurate recognition.
3. Regularization: Apply dropout techniques to prevent overfitting.
4. Validation and Testing: Split data into training, validation, and test sets. Evaluate diverse metrics to ensure balanced performance and conduct adversarial testing against spoofing.
REFERENCE
- V.V.D Shah “Image processing and its military applications”
- A.C Sleigh “Image understanding for Military Systems: A disscussion of the way forward for PRIP Research in Britain”
- Shengxi Gui, Shuang Song, Rongjun Qin and Yang Tang “Remote Sensing Object Detection in the Deep Learning Era”
- Yali Amit “Object Detection”
- Sergio Lima Netto, Eduardo A. B. da Silva, Rafael Padilla “A Survey on Performance Metrics for Object-Detection Algorithms”
- Alan Van Nevel, Jinhua She, Yingzi Du “Editorial Advanced Image Processing for Defense and Security Applications”
- G Militaru, M Panoiu, C Panoiu1 “Real-time detecting deformation on pantograph contact strip based on image processing technique”
- Dr. Megha Rani Raigonda, Shweta “Signature Verification System Using SSIM In Image Processing”


 Shivam Kumar*
Shivam Kumar*
 Enrique Anthony
Enrique Anthony
 Aditya Pardeshi
Aditya Pardeshi
 Shraddha Kashid
Shraddha Kashid



 10.5281/zenodo.14312670
10.5281/zenodo.14312670