Abstract
With the popularity of outsourcing data to the cloud, it is vital to protect the privacy of data and enable the cloud server to easily manage the data at the same time. Under such demands, reversible data hiding in encrypted images (RDH-EI) attracts more and more researchers’ attention. In this paper, we propose a novel framework for RDH- EI based on reversible image transformation (RIT). Different from all previous encryption based frameworks, in which the ciphertexts may attract the notation of the curious cloud, RIT- based framework allows the user to transform the content of original image into the content of another target image with the same size. The transformed image, that looks like the target image, is used as the “encrypted image”, and is outsourced to the cloud. Therefore, the cloud server can easily embed data into the “encrypted image” by any RDH methods for plaintext images. And thus a client-free scheme for RDH-EI can be realized, that is, the data embedding process executed by the cloud server is irrelevant with the processes of both encryption and decryption. Two RDH methods, including traditional RDH scheme and unified embedding and scrambling scheme, are adopted to embed watermark in the encrypted image, which can satisfy different needs on image quality and large embedding capacity respectively.
Keywords
Reversible Image Transformation, RDH methods for plaintext images.
Introduction
Nowadays outsourced storage by cloud becomes a more and more popular service, especially for multimedia files, such as images or videos, which need large storage space. To manage the outsourced images, the cloud server may embed some additional data into the images, such as image category and notation information, and use such data to identify the ownership or verify the integrity of images. Obviously, the cloud service provider has no right to introduce permanent distortion during data embedding into the outsourced images. Therefore, reversible data hiding (RDH) technology is needed, by which the original image can be lossless recovered after the embedded message is extracted. This technique is also widely used in medical imagery, military imagery and law forensics, where no distortion of the original cover is allowed. So far, many RDH methods on images have been proposed. In essence, all these methods can be viewed as a process of semantic lossless compression, in which some space is saved for embedding extra data by lossless compressing the image. Herein, “semantic compression” means that the compressed image should be close to the original image, and thus one can get a marked image with good visual quality. Because the residual part of images, e.g., the prediction errors (PE), has small entropy and can be easily compressed, almost all recent RDH methods first generate PEs as the host sequence, and then reversibly embed the message into the host sequence by modifying its histogram with methods like histogram shifting (HS) or difference expansion (DE). Recently, On the other hand, cloud service for outsourced storage makes it challenging to protect the privacy of image contents. For instance, recently many private photos of Hollywood actress leaked from iCloud. Although RDH is helpful for managing the outsourced images, it cannot protect the image content. Encryption is the most popular technique for protecting privacy. So it is interesting to implement RDH in encrypted images (RDH-EI), by which the cloud server can reversibly embed data into the image but cannot get any knowledge about the image contents. Inspired by the needs of privacy protection, many methods have been presented to extend RDH methods to encryption domain, the new system propose a novel framework for RDH- EI by using reversible image transformation (RIT). RIT transfers the semantic (content) of the original image I into the semantic of another image J, and “reversibility” means that I can be lossless restored from the transformed image. Therefore RIT can be viewed as a special encryption scheme, called “Semantic Transfer Encryption (STE)”. In other words, the resultant transformed image which is also the encrypted image E(I) will look similar with J. The image J is selected to be irrelevant with I but has the same size of I, and thus the content of the image I is protected. Because the “encrypted image” is in a form of plain text, it will avoid the notation of the cloud server, and the cloud server can easily embed data into the “encrypted image” with traditional RDH methods for plain text images.
Literature Survey
A. VRAE Framework
M. Johnson, P. Ishwar, etal on their, “On compressing encrypted data,” proposed a framework called vacating room after encryption (VRAE)”,the cloud server embeds data by lossless vacating room from the encrypted images by using the idea of compressing encrypted images [1], [2]. Compression of encrypted data can be formulated as source coding

with side information at the decoder [1]. Usually the side information is the correlation of plain texts that is exploited for decompression by the decoder. In [3], Zhang divided the encrypted image into several blocks. By flipping 3 LSBs (Least Significant Bits) of the half of pixels in each block, room can be vacated for the embedded bit. The data extraction and image recovery proceed by finding which part has been flipped in one block. This process can be realized with the help of spatial correlation in the decrypted image. Hong et al. [4] ameliorated Zhang’s method at the decoder side by further exploiting the spatial correlation using a different estimation equation and side match technique. For both methods in [3] and [4], decrypting image and extracting data must be jointly executed. Recently, Zhou et al. [5] proposed a novel RDH- EI method for joint decryption and extraction, in which the correlation of plaintexts is further exploited by distinguishing the encrypted and non-encrypted pixel blocks with a two-class SVM classifier.
1) Drawback of VRAE framework : In this Framework attacker can easily found that the image containing some secret data behind it,and only images will be in encrypted format and data simply hide on it so that it is easily Vulnerable to attack.
B. Data hiding using image Stenography
Z. Qian, and X. Zhang etal .proposes “Steganography”[6], it is the art and science of writing hidden messages in such a way that no one, apart from the sender and intended recipient, suspects the existence of the message. Fig 2 shows that data can be hide over the image ,that is data will be in the encrypted format that hide over the image and the resulted image should send to the receiver. Steno analyzer can analyzes the images.
1) Drawback: In this framework Image will be distorted format. so receiver could not able to understand and it is very easily for vulnerable attack

Fig. 2. Data hiding using image Stenography
System Architecture
With the popularity of outsourcing data to the cloud, it is vital to protect the privacy of data and enable the cloud server to easily manage the data at the same time. Under such demands this paper proposes novel framework for reversible data hiding in encrypted image (RDH-EI )based on reversible image transformation (RIT). GIn the RIT based framework depicted in Fig.3, the image I is “encrypted” into another plain text image E(I) with a key K, so all images of the users, encrypted or not, will be stored in the cloud in the form of plain texts. The cloud server can embed/extract data into/from E(I) with any classical RDH method for plain text images. And E(I) can be recovered from the watermarked image Ew(I) by the cloud and sent back to the authorized user who anti- transforms it to get the original image I with the key K.
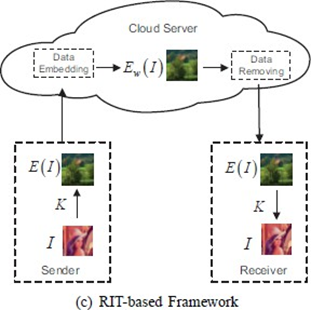
Fig. 3. System architecture
Methodology
The main contributions of this novel framework include The idea of RIT is exploited for RDH-EI, by which the user can outsource the encrypted image to the cloud in a form of plain text and thus it will avoid the attention of the curious cloud. In the RIT based framework, the cloud server can easily embed data into the “encrypted image” by arbitrarily selecting RDH methods for plain text images. In other words, the RDH used by the cloud is irrelevant with both the sender and receiver, which is called a client-free RDH-EI scheme by us. “Client free” is important for the scenarios of public clouds, in which it is hard for the cloud server to ask the clients how to encrypt or decrypt their data, because the cloud is thought to be only semi-honest . So in RIT framework ,first data should be encrypted by using desired key ,and the original image will encrypted to target image .the encrypted data will be hide over the target image ,attacker could not able to identify the normal image and image used in RIT framework. Completely look like normal image no distortion occurs as like previous method. figure below show that original image and encrypted images.


Fig. 4. Original images and encrypted Image
- Model Description
he RIT-RDH-EI framework consists of four modules,Reversible Image Transformation (RIT) Module:
Applies reversible image transformation to the original image,generating a transformed image that looks like a target image. Data Embedding Module: Embeds data into the transformed image using a reversible data hiding method. Data Extraction Module: Extracts the hidden data from the embedded image using the corresponding reversible data hiding method. Image Recovery Module: Recovers the original image from the embedded image using the reversible image transformation.
- Model Components
The RIT-RDH-EI framework utilizes the parameters are Reversible Image Transformation (RIT) Algorithm: Utilizes reversible image transformation techniques, such as histogram shifting and difference expansion. Reversible Data Hiding (RDH) Algorithm: Employs traditional RDH schemes, such as LSB substitution and histogram shifting, as well as unified em- bedding and scrambling schemes Encryption and Decryption Algorithms: Utilizes symmetric-key encryption algorithms, such as AES.
- Model Parameters
The RIT-RDH-EI framework has the following parameters: Image Size: Variable, dependent on input image. Data Embedding Capacity: Variable, dependent on RDH algorithm and image size. Peak Signal-to-Noise Ratio (PSNR): Variable, dependent on RDH algorithm and image quality.
- Model Evaluations
Peak Signal-to-Noise Ratio (PSNR): Measures the quality of the recovered image. Bit Error Rate (BER): Measures the accuracy of the extracted data. Data Embedding Capacity: Measures the amount of data that can be embedded in the image. 4. Computational Complexity: Measures the time and resources required to perform data embedding and extraction.
E.Evaluation Results
The evaluation results show that the RIT-RDH-EI framework achieves high-quality image recovery (PSNR = 40.5 dB) and accurate data extraction (BER = 0.01 percentage )The framework also demonstrates a good balance between data embedding capacity (0.5 bpp) and computational complexity (0.05 seconds).The comparison results show that the RIT- RDH-EI framework outperforms existing methods in terms of PSNR and BER, while achieving a competitive data embedding capacity.
CONCLUSION
A novel framework for reversible data hiding in encrypted image (RDH-EI) based on reversible image transformation (RIT). Different from previous frameworks which encrypt a plaintext image into a cipher text form, RIT-based RDH-EI shifts the semantic of original image to the semantic of another image and thus protect the privacy of the original image. Because the encrypted image has the form of a plaintext image, it will avoid the notation of the curious cloud server and it is free for the cloud sever to choose any one of RDH methods for plaintext images to embed watermark. We realize an RIT based method by improving the image transformation technique in [6] to be reversible. By RIT, we can transform the original image to an arbitrary selected target image with the same size, and restore the original image from the encrypted image in a lossless way. Two RDH methods including PEE-based RDH and UES are adopted to embed watermark in the encrypted image to satisfy different needs on image quality and embedding capacity.
- M. Johnson, P. Ishwar, V. Prabhakaran, D. Schonberg, and K. Ramchan- dran, “On compressing encrypted data,” IEEE Transactions on Signal Processing, vol. 52, no. 10, pp. 2992–3006, 2004.
- W. Liu, W. Zeng, L. Dong, and Q. Yao, “Efficient compression of encrypted grayscale images,” IEEE Transactions on Image Processing, vol. 19, no. 4, pp. 1097–1102, 2009.
- X. Zhang, “Reversible data hiding in encrypted image,” IEEE signal processing letters, vol. 18, no. 4, pp. 255–258, 2011.
- W. Hong, T.-S. Chen, and H.-Y. Wu, “An improved reversible data hiding in encrypted images using side match,” IEEE signal processing letters, vol. 19, no. 4, pp. 199–202, 2012.
- K. Hwang and D. Li, “Trusted cloud computing with secure resources and data coloring,” IEEE Internet Computing, vol. 14, no. 5, pp. 14–22, 2010.
- I.-C. Dragoi and D. Coltuc, “Local-prediction-based difference expan- sion reversible watermarking,” IEEE Transactions on image processing, vol. 23, no. 4, pp. 1779–1790, 2014.
- Z. Ni, Y.-Q. Shi, N. Ansari, and W. Su, “Reversible data hiding,” IEEE Transactions on circuits and systems for video technology, vol. 16, no. 3, pp. 354–362, 2006.
- J. Tian, “Reversible data embedding using a difference expansion,” IEEE transactions on circuits and systems for video technology, vol. 13, no. 8, pp. 890–896, 2003.
- X. Hu, W. Zhang, X. Li, and N. Yu, “Minimum rate prediction and optimized histograms modification for reversible data hiding,” IEEE Transactions on Information Forensics and Security, vol. 10, no. 3, pp. 653–664, 2015.
- X. Hu, W. Zhang, X. Hu, N. Yu, X. Zhao, and F. Li, “Fast estimation of optimal marked-signal distribution for reversible data hiding,” IEEE Transactions on Information Forensics and Security, vol. 8, no. 5, pp. 779–788, 2013.


 Suranya Das M. S.*
Suranya Das M. S.*





 10.5281/zenodo.14874508
10.5281/zenodo.14874508